We got reported today in the morning (European time) three bugs that work on community and enterprise. They are not serious (they can not mingle your data) but anyway we fixed them already for enterprise. The fix took 5hs from reporting (can anyone remind me which vendor provides a patch in 5 hours please?).
The details (from extracts on our email conversation with the guy that reported them):
The vulnerabilities are:
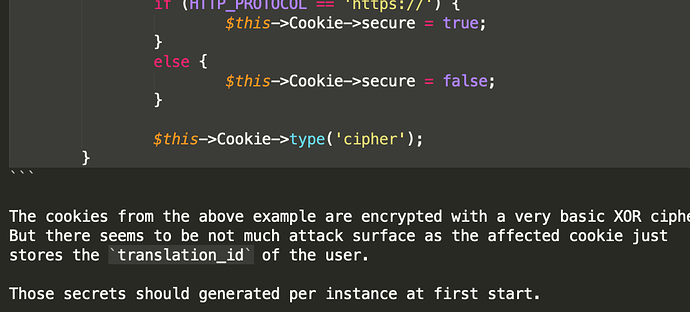
1- Hard coded secrets (eramba_static_secrets.md)
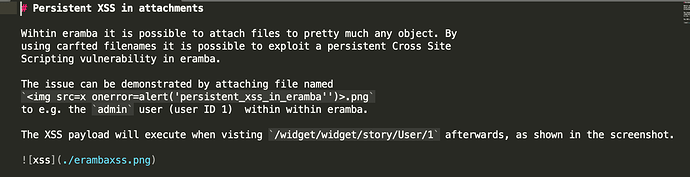
2- Persistent cross site scripting (eramba_persistent_xss.md & erambaxss.png)
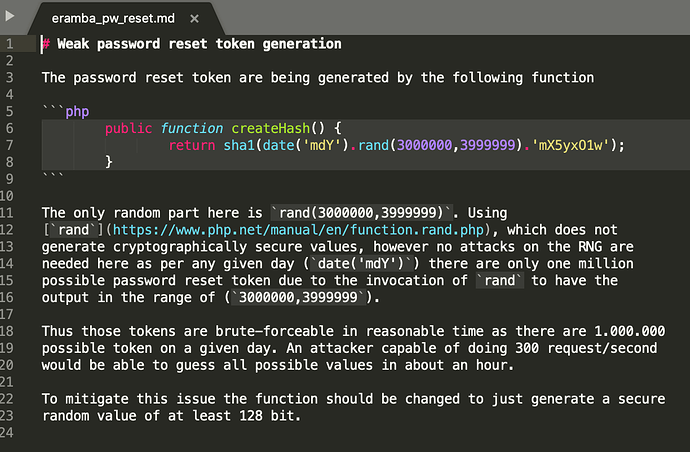
3- Weak password reset token generation (eramba_pw_reset.md)
A summary on them:
1- is not really relevant so nothing was or will be done with this for a long time
2- this means that if a person HAS an account in eramba and CAN login (this means you know who the person is and you trust otherwise they would not have an account) , that person can upload as attachment a file with XSS embedded and that will load when the same (or another user) clicks on the attachment. This of course is a bit unlikely as whoever upload a file will need an account and it would be evident who the perpetrator was (the trails are on the modal). This is fixed by sanitising output on attachments.
3- When you “lost a password” (ONLY if you are using local accounts, most people uses LDAP and therefore this is not applicable) you can “recover” them if you forgot them, eramba will send an email with a token (valid for 24hs). In theory (this has not been tested as is unlikely to work) you could try to brute-force the token (if you know the url) by trying 300 (or more) keys per second non stop for one hour. Frankly speaking no eramba deployment can stand 300 requests per second without going down so we see this again very unlikely. Anyway is fixed by reducing the window to one hour and making the token more complicated (before 6 random characters now 50)
We want to thank “Joern Schneeweisz from the GitLab Security Research Team” because instead of sending a dull tool report which is almost never useful he took time and debug this and showed us in detail how to reproduce these issues. It took 5 hours issue a fix but im sure it took another couple of hours to find them !
Community will get these and many many other bugs fixed on the anual upgrade which will take place around November. Enterprise has a fix on e2.19.3.