Hello,
Context
We have strict regulations to respect regarding access & authorizations, one of them being to be able to identify who connected to a system, when, and why.
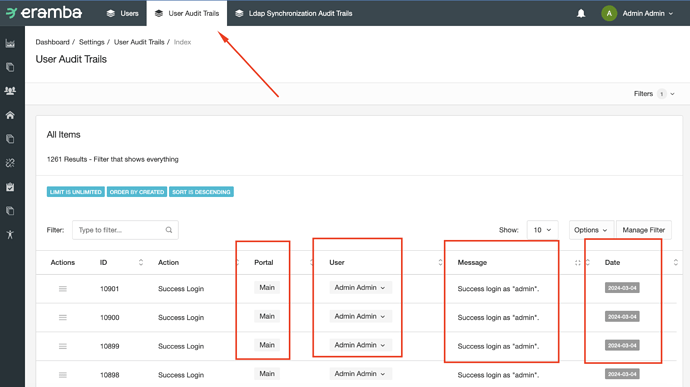
As far as I have seen, Eramba allows to see audit trails, but they are difficult to exploit as is. The usernames are masked (which is making impossible to differentiate who connected to the system in our case, as our accounts are following a specific naming convention). All our logs are stored into a Splunk for further exploitation. However, the audit trails are currently unusable.
I understand that this is because the application’s logs are regularly sent to Eramba, if the user chooses too. On an external point-of-view, it makes sense to mask the potential sensitive information in that case. On an internal point-of-view, it does not make sense and impair the monitoring process.
Feature request
-
Keep local logs unmask to allow internal processing.
-
Mask sensitive information from the logs once they are sent to Eramba (so only if the user has enabled “Help improve Eramba’s features and performance”).
-
Allow the users to choose what logs to send to Eramba. I understand why you need error log, or system health status log. I don’t understand why, for example, the access, authentication, and authorization logs are useful.
Thanks.