Hi There,
We’ve deployed the community version of Eramba, and now the enterprise version, following the steps in here for connecting to Azure AD for SAML Auth.
Question - SAML Configuration for Azure AD - Settings - eramba
I’ve discovered that the Azure Enterprise application breaks with the enterprise version. Within the enterprise version I can test SSO, and it works, however actually using SSO fails because it looks like the redirect URL’s have been hard coded in the enterprise version to use http.
In the SAML connector in the community version, I see the Redirect URLS listed like:
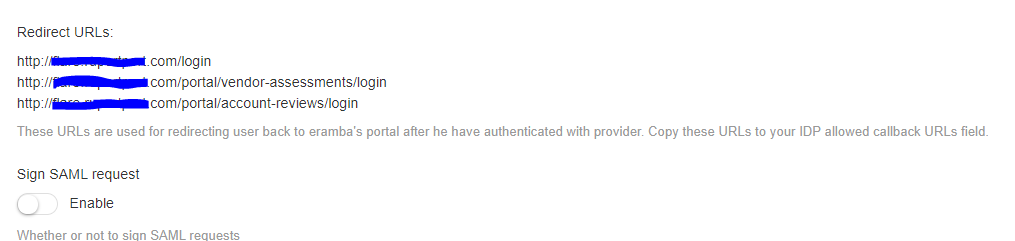
In the enterprise version I see them as:
Also, on the community version the Sign SAML Request is enabled even though I haven’t entered x509 certs or keys (and it works fine). If I toggle the Sign SAML on the enterprise version it forces me to enter x509 cert and key, but I’m not currently using that.
Hopefully I’ve described this properly.
With regards,
Tim