Hello Erambateers.
I come to your forum, seeking aide, guidance, advice, and solace. I’ve trawled this forum and the learning documentation for answers, and have come up short.
Context
I’ve just started the process of deploying Eramba (Community) to evaluate it for use in our organisation. We like the feature set on paper, but making sure it does what it says it does is kind of important. We would be looking to move to an enterprise package if this solves our current problem, which is that the executive would like to get a better handle on risk and compliance.
At the moment, everything is going swimmingly, and following the learning documentation journey has been straightforward - if not long winded. It’s better than the alternative of short and meaningless documentation, though, or none at all.
Work and troubleshooting so far
We have a Keycloak deployment where we mostly use OIDC, but can support SAML in a pinch if that’s all that’s available. We’re trying to phase out LDAP traffic where possible.
I have set up Eramba using the Docker Installation method. We are additionally running this behind an NGINX reverse proxy to our DMZ so that Keycloak and Eramba can talk to each other. This hasn’t caused issues for other SAML apps in the past.
Eramba App Version: 3.24.2
DB Schema Version: 20240605095337
So far, I have followed the limited guide on configuring SAML for Eramba, but it’s heavily focussed on Azure AD SAML, and there’s not much information about any settings other than the Azure AD SAML video in the documentation portal.
I have:
- Set up the SAML authentication connector in Eramba
- Set up the client and client scopes in Keycloak based on the information from the connector
- Confirmed communication between the two
- Enabled the authentication connector as SAML in Eramba
- Switched a user from Local to … not local … which means it should be identified by SAML connector.
These should be all the required steps to get it working, however we ran into the issue described in : Question - SAML using Keycloak as IdP - #5 by steelem
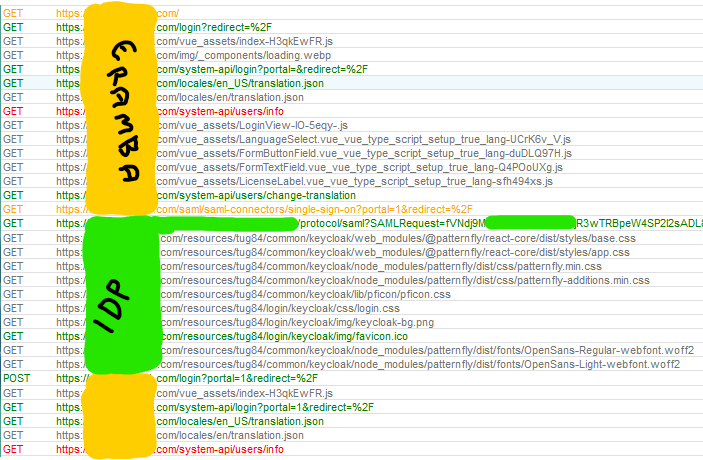
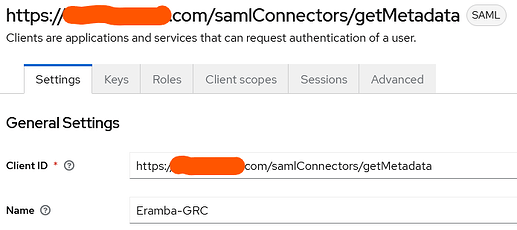
As with the above issue, we were getting “Invalid request” from keycloak; notably, the connector says to use <fqdn>/saml/saml-connectors/get-metadata but in the SAML packet information we can see it needed to be <>fqdn>/samlConnectors/getMetadata. This matched what I saw in the other forum post. We changed this setting in the Keycloak client settings, and the SAML request started working from Eramba to Keycloak.
Once I authenticate with Keycloak, the SAML response is returned to Eramba, seemingly successfully, but Eramba doesn’t do anything with it.
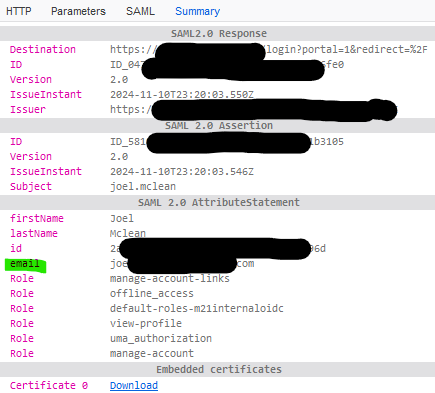
I have tried a few variations on the user; at the moment, the user is set so that both the username and email address fields are the users’ email address, but my preference would be to have the username be “user.name” format, not email address. I’d rather it be working than not, so if that’s non-negotiable, then so be it.
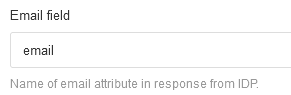
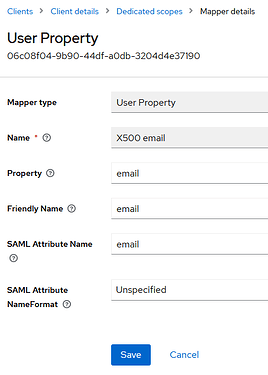
I can confirm that in my SAML response to Eramba, the SAML parameters include the “email” attribute, and in Eramba I have the identifier as “email”.
The SAML “subject” is user.name, as that’s our model, but Eramba should only be looking at the email field defined in the connector.
My actual question
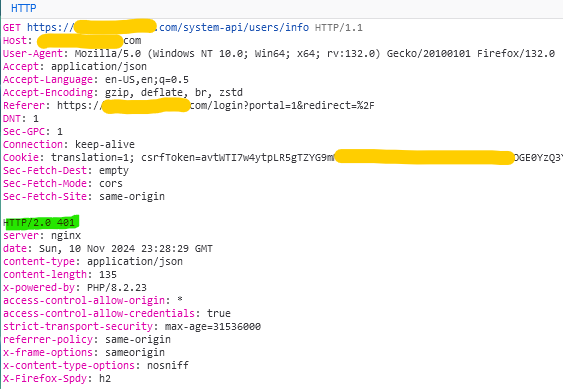
Nothing is in the logs (authentication.log) at all, not even a failed attempt. The only logs that are changing are the access log and the debug log, neither of which are showing anything relevant (other than 401 unauthorised in the access log)
I would have expected to see a log from Eramba when it receives the SAML response, and fails to find a matching user, it should log that somewhere.
What am I missing? Do I need to turn up authentication logging? If so, how?
My best guess is that Eramba is seeing the SAML response, and is not matching it to a user.
I am getting no error, no feedback, and no logs on the server side, and no error in the browser on the client side - the only way I was able to determine for sure it should be working and isn’t was by using a browser extension to inspect the SAML information, and compare it to one of our other SAML apps.
So, does anyone have any ideas? I spent a few hours trying to get this to work, but without logs, or clearer documentation about the SAML connector settings, I’m spinning my tires.
NB: As an aside, this forum looks like it might be Gitlab, which is big chops. We also run gitlab internally, and love it.